Technical Insights
Deep dives into ESLint security, JavaScript performance, and modern development practices.
The 30-Minute Security Audit: A Static Analysis Protocol for Onboarding
A data-driven protocol for assessing a new codebase in under 30 minutes. Use automated static analysis to generate immediate risk heatmaps for CTOs and VPs.

We Ranked 5 AI Models by Security. The Leaderboard Is Wrong.
Claude Opus generates vulnerable JWT code every single time — 7 out of 7 runs, always leaking...

The AI Hydra Problem: Fix One AI Bug, Get Two More
When AI models fix security vulnerabilities, they sometimes introduce entirely new ones. I tested this across 3 remediation rounds with Claude Opus 4.6 using two approaches — ESLint-guided feedback vs. prompt engineering alone. The results expose a fundamental limit of 'fix it again' workflows.

Microsoft's ESLint Security Plugin Catches 10% of Vulnerabilities. Here's What It Misses.
A head-to-head benchmark between @microsoft/eslint-plugin-sdl and the Interlace security ecosystem. Microsoft's SDL standard covers 1 of 14 security categories.

SonarJS Has 269 Rules. It Still Misses 65% of Security Vulnerabilities.
A head-to-head benchmark between eslint-plugin-sonarjs and the Interlace security ecosystem. 269 rules vs 201 rules — more isn't better when 65% of vulnerabilities slip through.

eslint-plugin-security Is Unmaintained. Here's What Nobody Tells You.
eslint-plugin-security has 1.5M weekly downloads but only 13 rules and no meaningful updates since 2020. Learn why it misses 90% of vulnerabilities—including SQL injection, JWT attacks, and AI/LLM security—and what modern ESLint security plugins to use instead.

I Let Claude Write 80 Functions. 65-75% Had Security Vulnerabilities.
AI coding assistants are incredible—until they introduce security holes. I ran an experiment asking Claude (Haiku 3.5, Sonnet 4.5, Opus 4.5, Opus 4.6) to generate 80 common Node.js functions with zero security context using my Claude Pro subscription. 65-75% had vulnerabilities. Then I tested if static analysis could help the models fix their own mistakes.
Exploit Analysis: PostgreSQL COPY FROM Filesystem Access
A deep dive into PostgreSQL filesystem exploits. Learn how to engineer static analysis guards to prevent unauthorized database-level file access.

The Performance Protocol: Solving PostgreSQL N+1 Loops via Static Analysis
Eliminate API performance bottlenecks at the commit level. A case study on detecting and fixing architectural N+1 patterns programmatically.
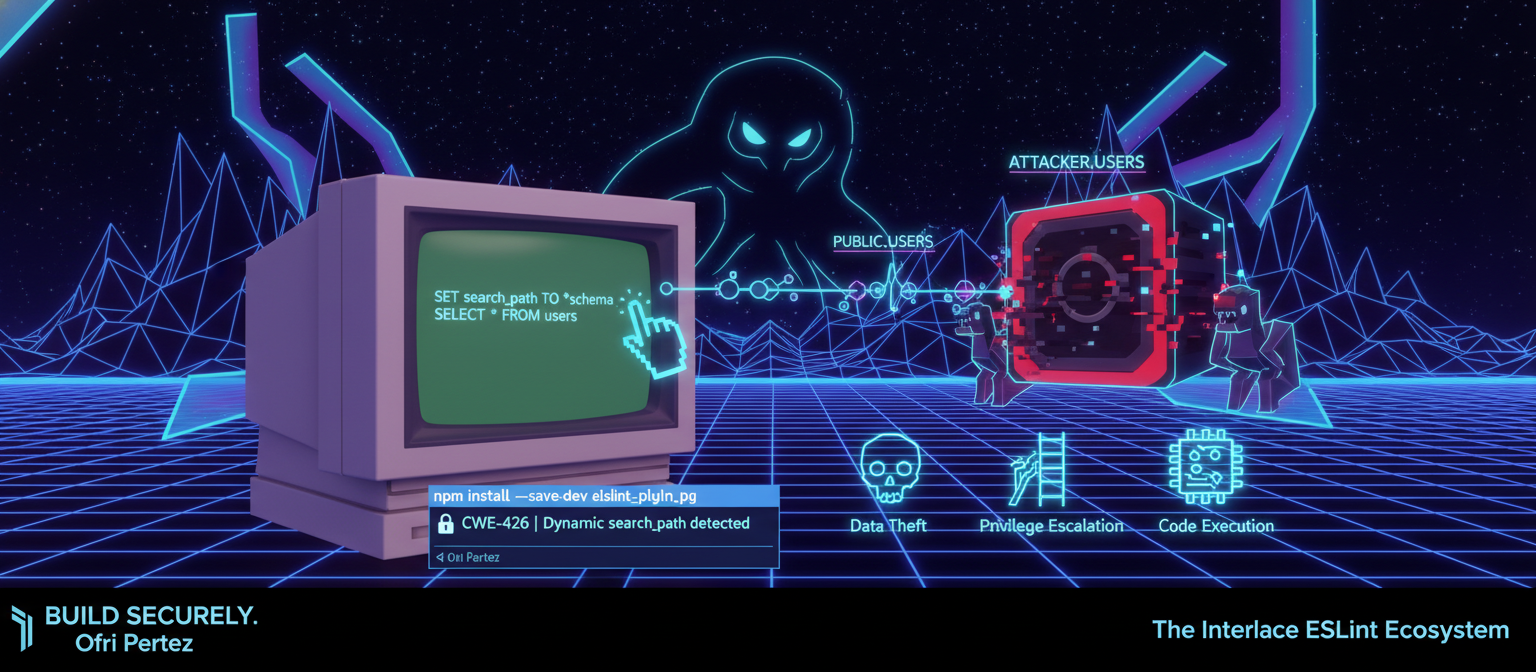
Exploit Analysis: search_path Hijacking (The Hidden PostgreSQL Attack)
Engineering against architectural vulnerabilities. A professional analysis of search_path hijacking and the static analysis standard for prevention.